Introduction
As some of you may know I own a company called Offensive AI http://offensiveai.com/ . Our mission is to create the worlds first virtual penetration tester utilizing AI/ML. One of our first projects is to tackle the external environment and that’s where bug bounties come in. We created a framework to automate the vast majority of the recon & fingerprinting phase leaving the explanation phase to you.
You can get the tool here:
https://bounty.offensiveai.com/
Free Version or Paid
So, to give a little something back to the community and to give you a little taste of the product I created a free version of the tool. This will give you limited access to the platform so you can get your feet wet.
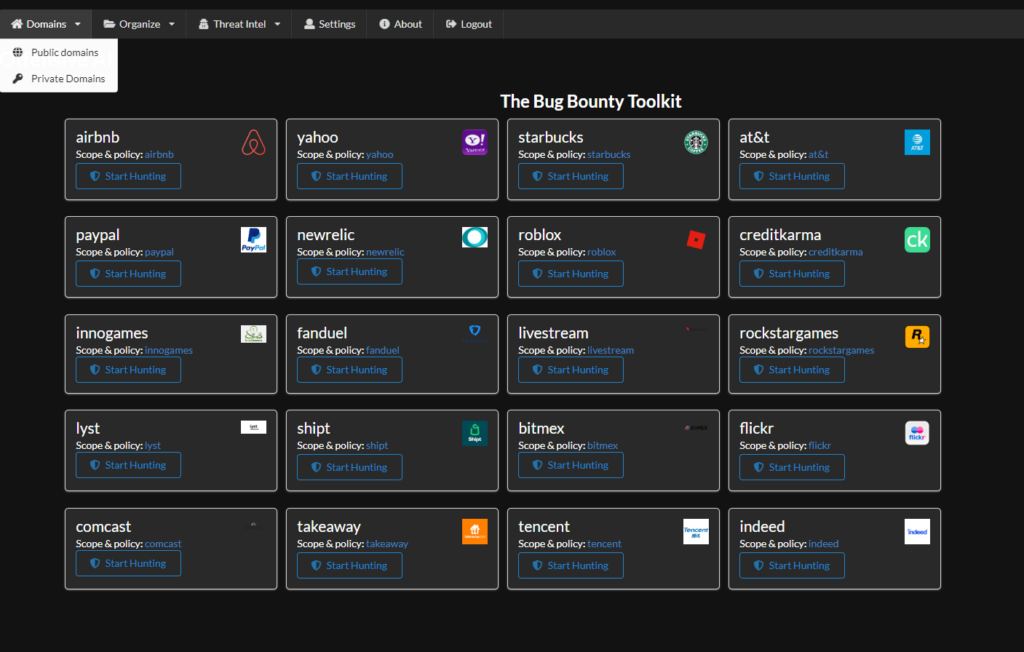
If your using the paid version you will have the ability to track private domains. So if you have a private program, pentest engagement, or what ever you can track it.
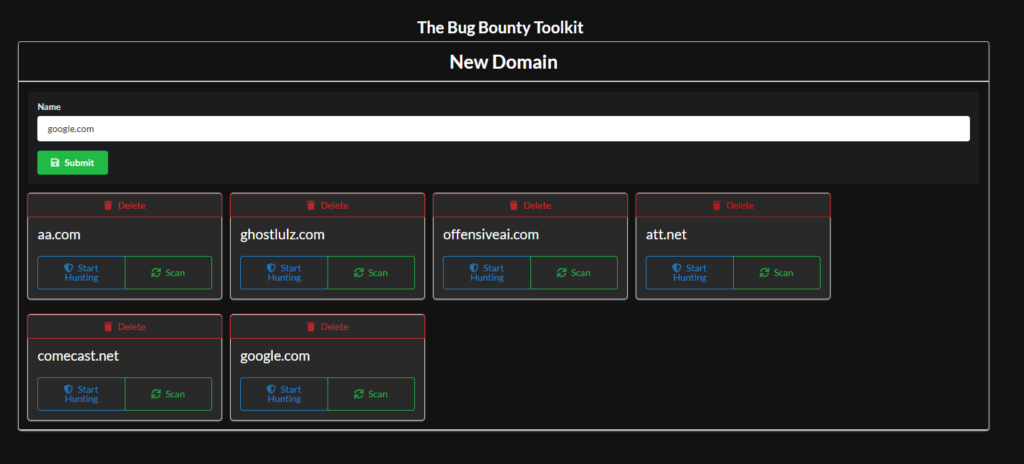
To add a domain just type it in and press submit. You can then initiate the scan process by hitting the green button labeled scan. This will put the domain in a queue to be scanned, the process typically take 10-45 min but it will automate the entire recon & fingerprinting phase. We handle the subdomain enumeration, portscans, banner grabbing, fingerprinting, screenshots, saving http requests, gathering dns information, and much more.
Whats nice is that you can just fire off a bunch of domains go watch a netflix show, come back, and all your recon & fingerprinting will be done, you just have to do the exploitation phase. Doing this process on this many domains could take days or weeks, my tool does it in an hour or two.
Threat Intel
One of the best sources of security intelligence is twitter. When new CVEs drop you can find them on twitter, when new exploit code is dropped the authors mentions it on twitter, want to know about CSRF,XSS,Auth bypasses there prob a link to someones blog on twitter about that topic.
Now one of the things I often come across while hunting is web application firewalls (WAFs). Instead of trying to figure out a bypass my self I typical turn to twitter for the latest and greatest one.
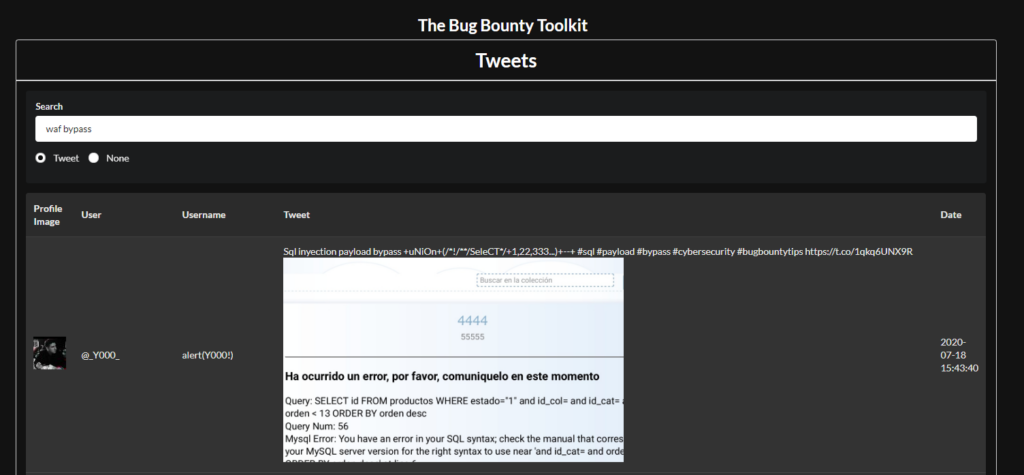
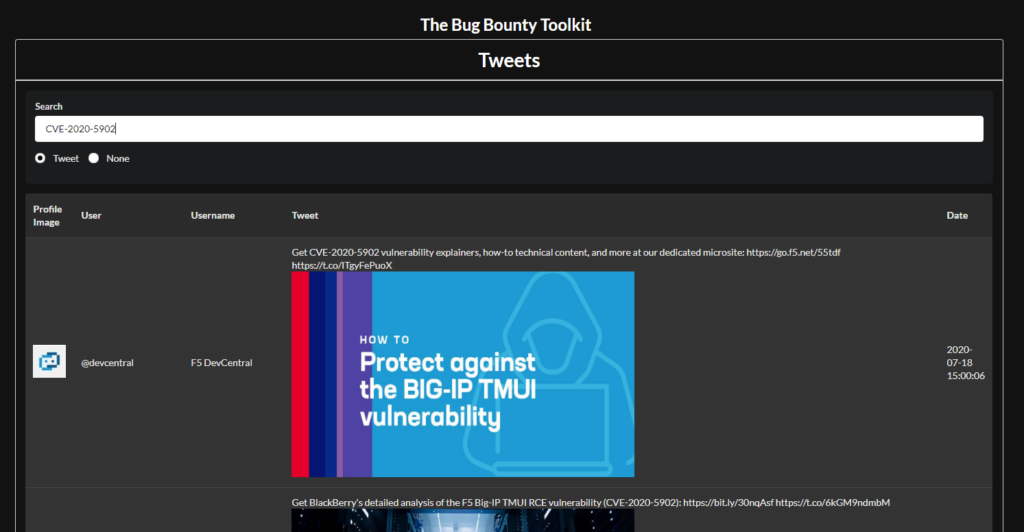
I also like to mine twitter for proof-of-concept (POC) code to new CVEs. Finding exploit code is very easy simply search for “CVE-XXX-XXX POC” or “CVE-XXX-XXX github”
I can go on all day about the different ways I use twitter to mine for interesting information but I wont bore you.
In addition to twitter I use RSS feeds to get live updates on new exploits, CVEs, and security news. As a hunter you really need to make sure you stay on top of whats happening in the security world. Things move very quickly and you need to be ready to pounce on new exploits as they come out, these are easy wins all day.
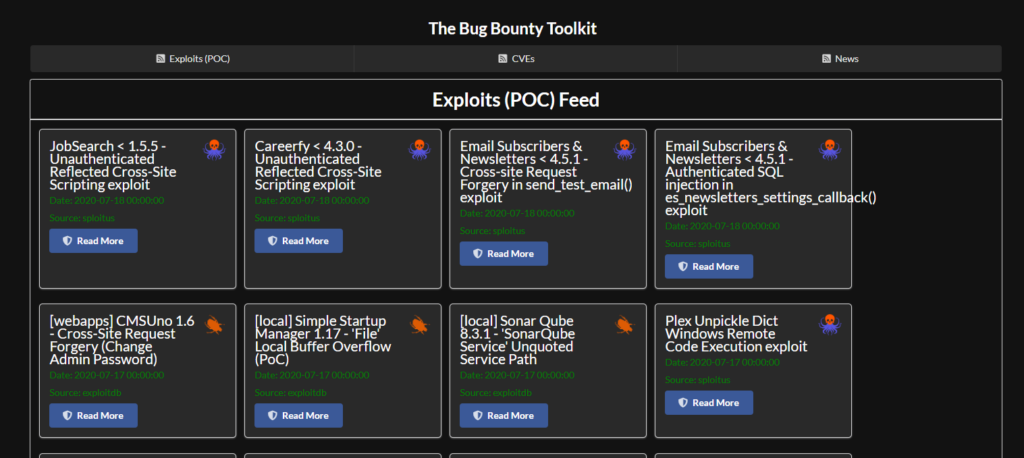
As you can see above I am tracking exploitdb and sploitus for new exploit POCs. I look at this everyday and if I see something I know is running in a target environment I will run it against them. The key here is being the first person so make sure you check out the newly released exploits daily.
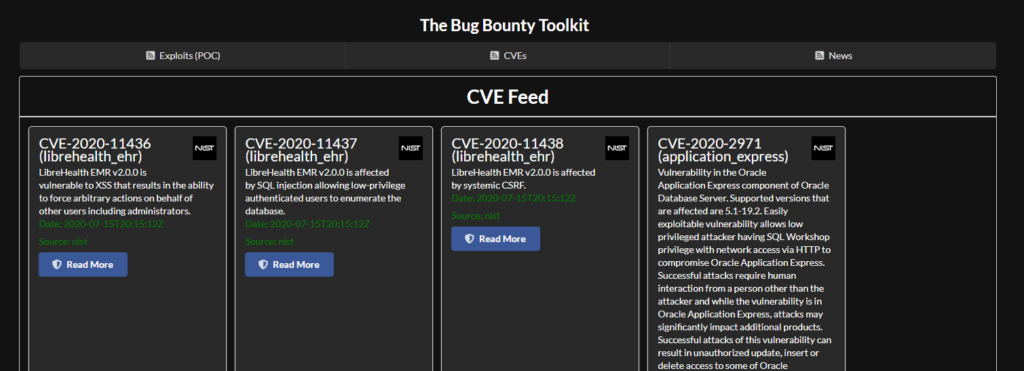
You also need to watch for new CVEs. Sometimes a POC wont make it to exploitdb for a week or two, and you need to know exactly when new vulnerabilities come out. Generally when I see a new CVE that looks interesting ill search for it on twitter, github, and google looking for exploit code or tutorials explaining the exploits.
One-days can be a bug bounty hunters best friend, you just need to stay on top of whats happening in the security world. You dont want to be that person who missing 5k because you didnt release a new citrix RCE came out.
Dashboard
After clicking the blue “Start Hunting” button on a domain you will be directed to the dashboard screen as shown below:
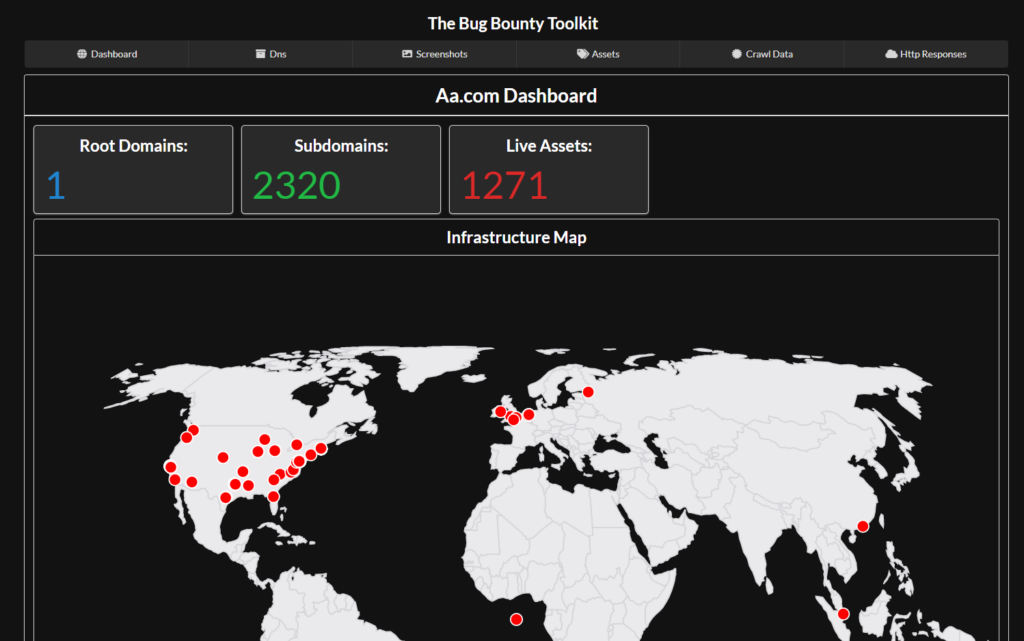
One of the first things you see is the total number of domains, live assets, and a map of the companies infrastructure. Note when looking at the assets an asset is a host:port combination so “example.com:22” and “example.com:443” are two different assets.
If you scroll down a little you will see some charts. The first chart is a bar graph of the companies fingerprints.
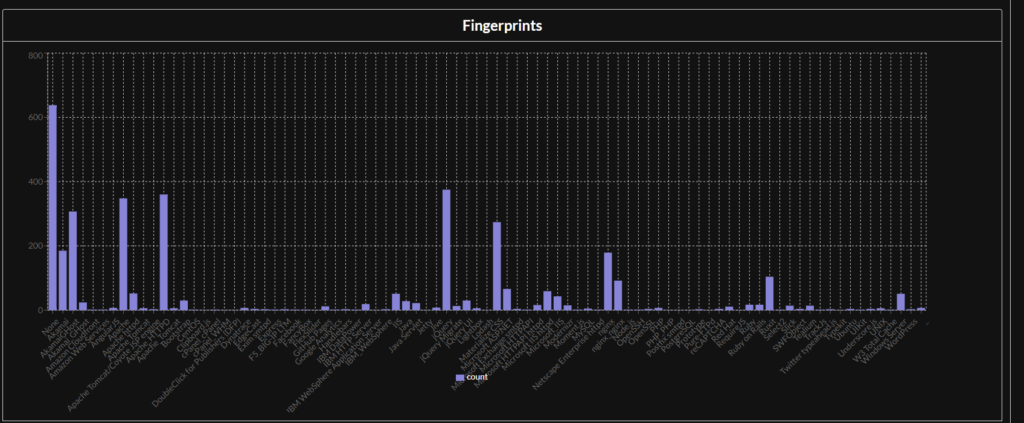
This chart is extremely important as it gives you the layout of an organization technologies. I will after scroll through here looking for interesting technologies like jira, adobe experience manager, cisco, vmware, outlook, and other devices. If you know citrix just had a new CVE drop and you see a citrix device in the fingerprints then you might have a winner.
Also pay attention to the services and ports pie graph, this is great for finding ports and services that contain misconfigurations. For example I often search for the elasticsearch port because its often left wide open with out auth. I also like looking services with logins such as vnc,ssh,and rdp as these are great for bruteforcing.

Remember look for those easy wins. Look out for technologies with known CVEs, ports with known attacks, and any other easy win.
Assets
So by now you should have some interesting technologies, ports , or endpoints you want to search for. This is where the assets tab comes in.
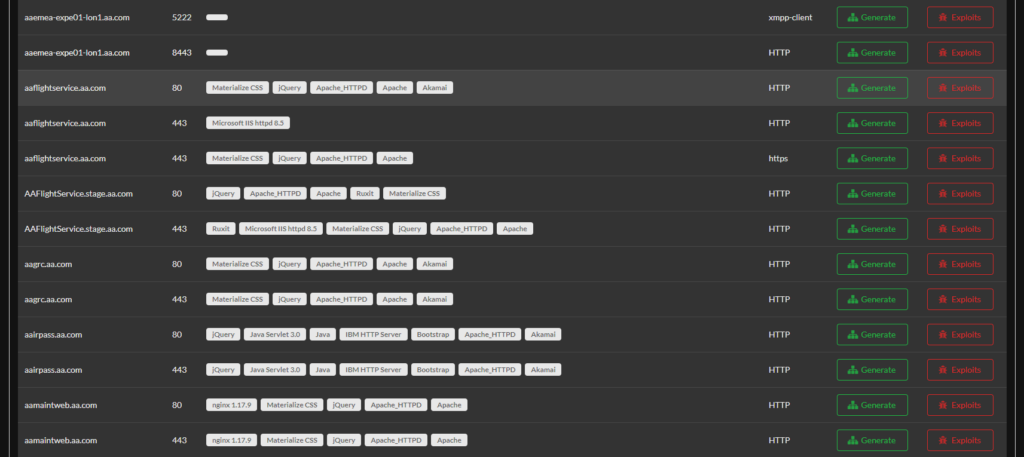
While looking at the dashboard I saw some interesting fingerprints and I can search for those endpoints as shown below:
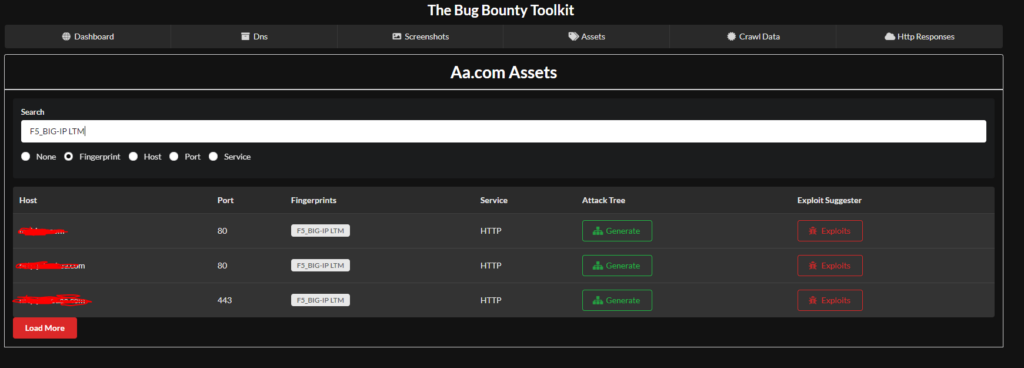
Thats an F5 Big IP and at the time of writing this there was a new exploit out in that. All you need is some exploit code and your off. Easy wins!
I also mentioned that I like brute forcing, if you switch to the service tab and search for “ssh” you will get a bunch of endpoints to target.
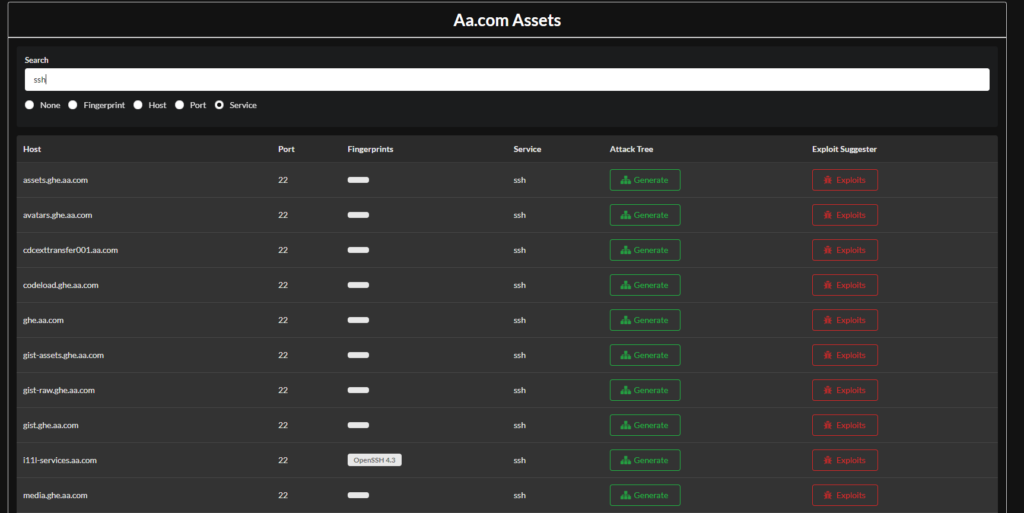
Searching like this your options are really limitless. All you have to do is find an interesting tech stack, port, or service and search for it. Once you get some results launch your attack.
Your not just limited to searching for fingerprints and ports. I also like to search for sites that contain certain words. For example if I see any of the following words im always interested:
- admin
- stage
- test
- vpn
- etc
The list can go on, but if you want to find interesting targets this this a great way just search by host as shown below:
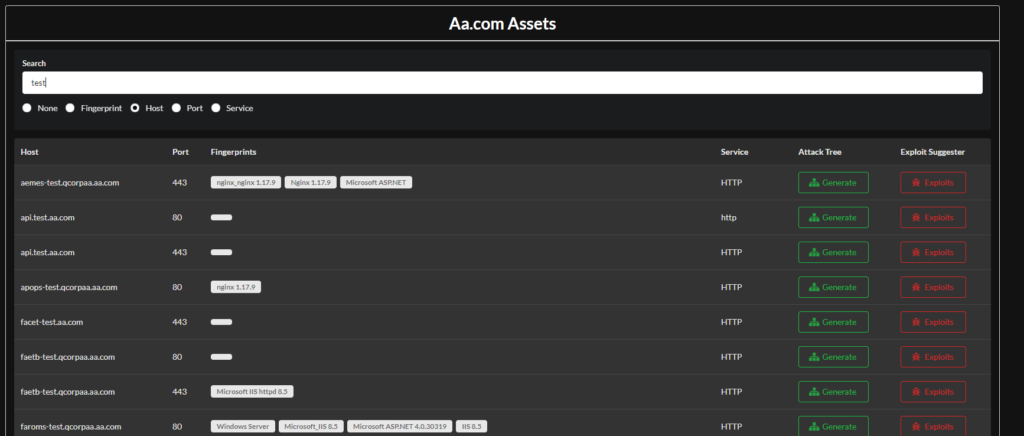
As you can see I search for domains containing the word “test” I got a bunch of results back and I can assume all of these sites are test environments so they may not be as harden.
Screenshots
The screenshots functionality is by far peoples favorite. It is extremely easy to spot vulnerabilities by simply browsing at screenshots. People find all kinds of things like:
- Directory Listing
- Open S3 Buckets
- Subdomain Takeover
- Information disclosures
- Stack Traces
- Old looking sites you know are vulnerable
- etc
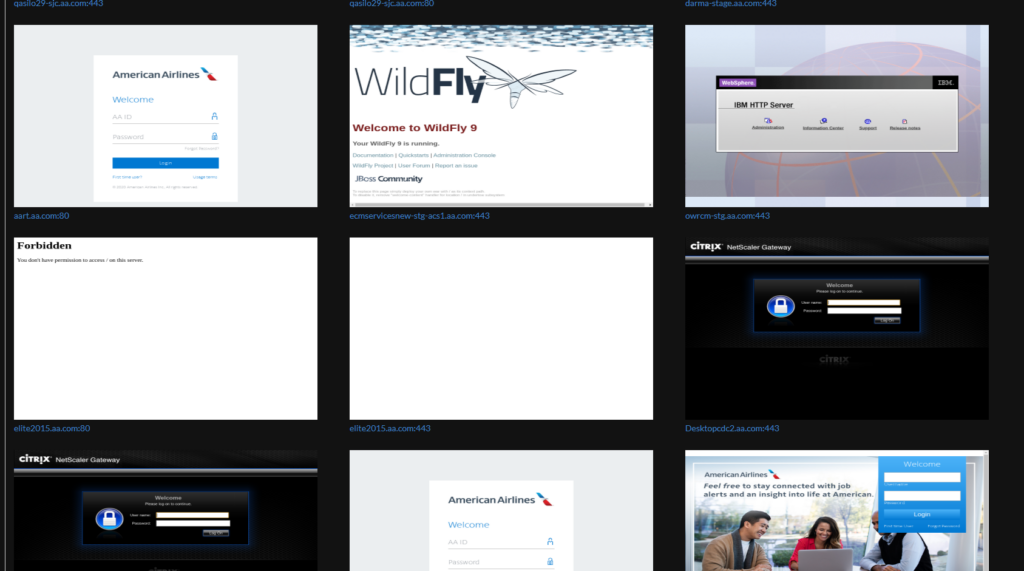
Just looking at the above images I see all kinds of things I can test for. If you know what to look for this methodology becomes extremely easy and very dangerous.
Crawl Data
When performing an engagement against a web applications one of the first things some people do is crawl the site. After you gather a list of urls you can use parameter mining techniques to find possible vulnerabilities. For instance you might search for the following GET parameters to find certain vulnerbilties:
- Open Redirect
- redirect=
- r=
- url=
- JSONP
- callback=
- jsonp=
- XSS
- url=
- error=
- Etc
The list can go on forever but parameter mining is great at finding potentials vulnerabilities.
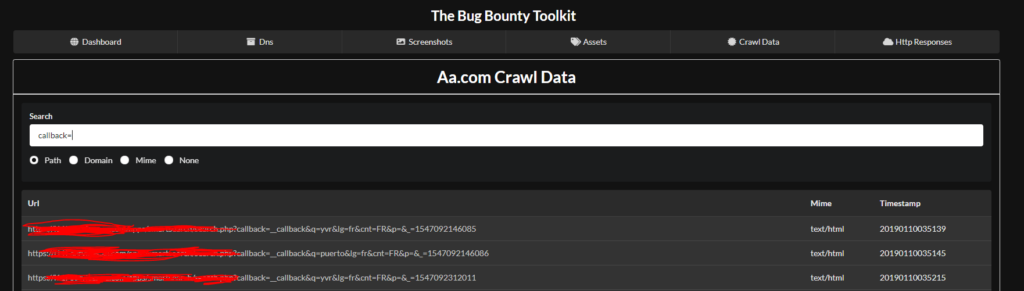
As shown above I searched for the GET parameter “callback” and got a few potential vulnerabilities, test have to test to find out.
In addition to parameter mining you should also be looking for information disclosures there have been a few people reporting those with my tool. Crawling is done for every domain(just like everything else) so if your hunting on a large site you could spend days on this tab looking at interesting things, there is so much stuff, its awesome!
HTTP Responses
This is another really handy feature. Here you search through the responses of every site the tool scanned. I often use this to find fingerprints which arnt in my tool. For example if I want to find all gitlab servers I might search the http body for the word “gitlab”. This is extremely powerful .
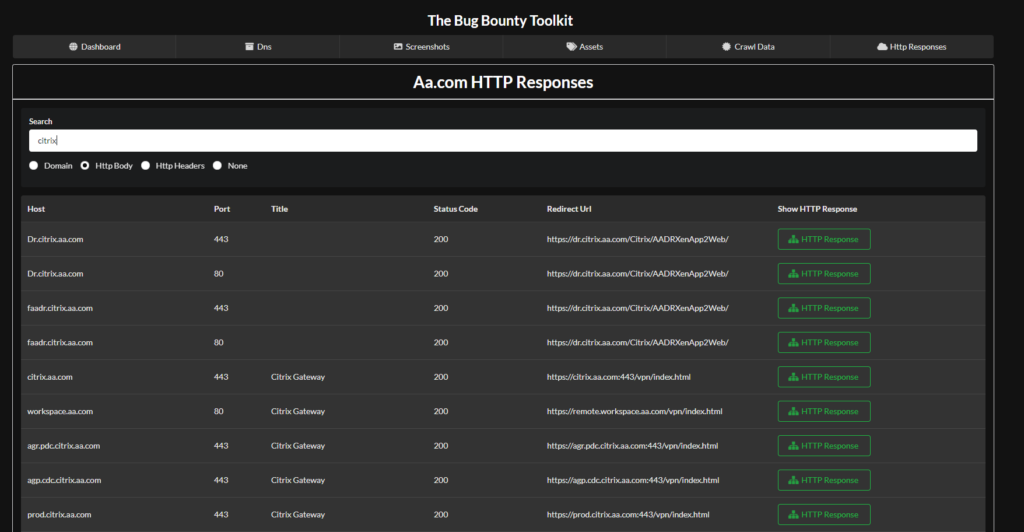
As you can see above I search for the word “citrix” which returned a bunch of results. Looking at the title column you can easily determine what each device is. I often just scroll through here looking at the “Title” column for interesting endpoints, iv found all kinds of stuff this way.
DNS
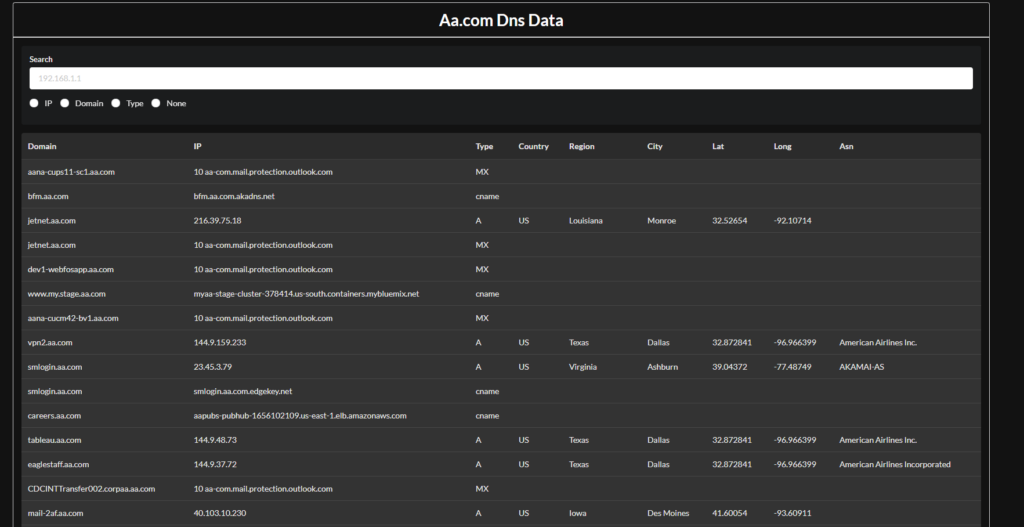
If your looking for DNS information we also track that. The main reason for this is because I like looking for CNAMES, and MX records. CNAMES are associated with subdomain takeovers and MX records correlate to mail servers.
Ill also like to look at the ASN organization which inform me if my target uses AWS,google cloud, or their own infrastructure. This is important because stuff hosted on AWS are heavy impacted by SSRF vulns so thats good info to know. Also assets hosted on their own infrastructure is probably more criticle and could lead right into their internal network.
Conclusion
This is what nextgen bug bounty software should look like. Our tool completely automates the entire recon & fingerprinting phase saving you weeks of time and it presents the data to you in an easy to consume manner. As of right now several of the top bug bounty hunters use this tool to automate their process.
Do you want easy wins? Are you looking to get more bugs so you can make more money? Are you looking to spend less time on recon and more time hacking? Are you looking to automate your process and save hundreds of man hours? Are you looking for nextgen technology that hits with the power of a nation state? If you answered YES than this tool is for you.
Hmm it appears like your blog ate my first comment (it was super long) so I guess I’ll just sum it up
what I wrote and say, I’m thoroughly enjoying your blog.
I too am an aspiring blog writer but I’m still new to the
whole thing. Do you have any points for beginner blog writers?
I’d definitely appreciate it.
Great blog here! Also your website loads up fast! What web host are you
using? Can I get your affiliate link to your host?
I wish my website loaded up as quickly as yours
lol
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed in Yahoo News?
I’ve been trying for a while but I never seem to get there!
Thanks
Also visit my web page – fb88
Thank you for the good writeup. It in reality was
once a entertainment account it. Glance advanced to far introduced agreeable
from you! By the way, how could we keep in touch?
Wonderful blog! I found it while browsing on Yahoo News.
Do you have any tips on how to get listed in Yahoo News? I’ve been trying for
a while but I never seem to get there! Appreciate it
my page Dulayhan
Usually I do not read post on blogs, however I wish to say
that this write-up very pressured me to take a look at and do it!
Your writing taste has been surprised me.
Thanks, quite nice article.
Feel free to surf to my web page; fb88