Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
Any site that starts with HTTPS:// uses SSL certificates to provide a secure connection. If a hacker or rogue certificate authority is able to forge this certificate they would be able to perform man in the middle attacks. To help thwart rogue certificate authorities from creating fake SSL certificates the certificate transparency log was created.
Certificate Transparency Log
The certificate transparency log is used to monitor and audit unauthorized certificates. Every time you get a SSL certificate for your domain or subdomain it will be logged in certificate transparency logs.
We can take advantage of this behavior to help enumerate subdomains belonging to a domain. There are tools out there that go out and gather all the transparency log files and store them in locally in a database. However, in this blog im going to be utilizing the site CERT.SH .We can find all SSL certificates belonging to a domain by issuing a GET request to https://crt.sh/?q=%25.facebook.com as shown below:
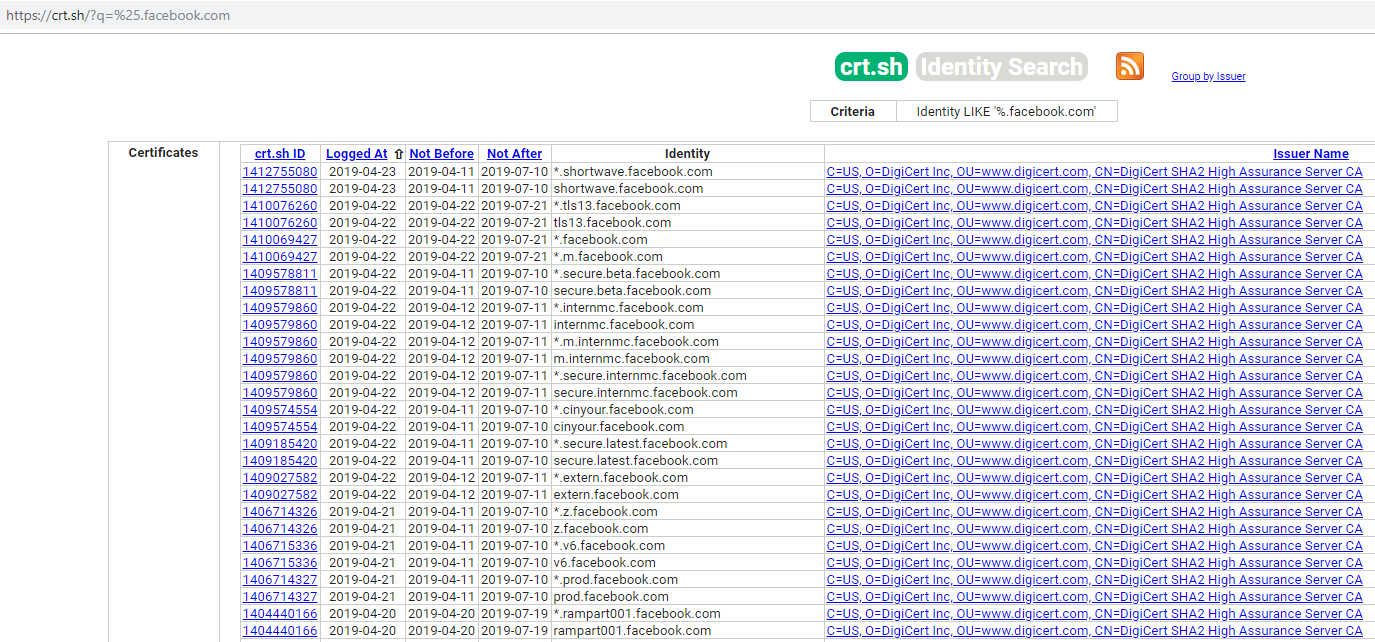
As shown above you will be presented with a huge list of subdomains. Many subdomain enumeration tools use certificate transparency logs as part of their enumeration process. Though there are tuns of tools that do this automatically behind the scenes but its always nice to have a deeper understanding of whats happening under the hood.
Tools
Feel free to browse the site in your browser but I personally like using the command line and a python script as its easier to parse out the subdomains.
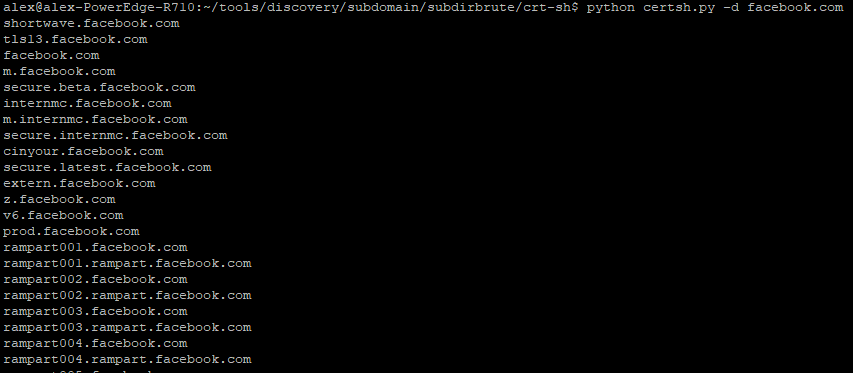
If you want to use the command line for this checkout my tool I created to extract subdomains from cert.sh: ghostlulzhacks/CertificateTransparencyLogs
Contribute to ghostlulzhacks/CertificateTransparencyLogs development by creating an account on GitHub.github.com
Again most subdomain enumeration tools use this technique in combination with others when finding subdomains.
Conclusion
Certificate transparency logs contain a list of all websites who request a SSL certificate for their domain. These logs were created to help spot forged certificates but we can use them in our subdomain enumeration process.