Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
Source code repositories like github are extremely popular. A lot of people will simple copy down a git directory and throw it on there website without realizing they might have just exposed their sites source code to the world. Git and Subversion are two of the most popular revision control systems and they contain a hidden file that can cause a lot of harm if uploaded to your website.
Git
Git is a revision control system and it contains a hidden folder “.git” . This folder basically acts as a snapshot for your project. Every-time you create a file git will compresses it and stores it into its own data structure. The compressed object will have a unique name, hash, and will be stored under the object directory. This means that you can fully re create the source code and everything else in the repository. If you navigate to “https://example.com/.git” and you see the following then that endpoint is vulnerable:
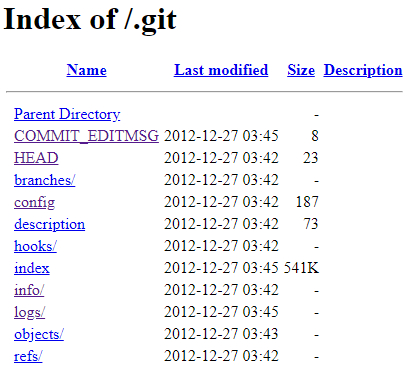
You can then recreate the repository which will contain the websites source code. To recreate the repository you can use the following tool:internetwache/GitTools
A repository with 3 tools for pwn’ing websites with .git repositories available – internetwache/GitToolsgithub.com
To use the tool simple type “./gitdumper.sh https://example.com/.git/ /output-directory/”. This will clone the entire repository.
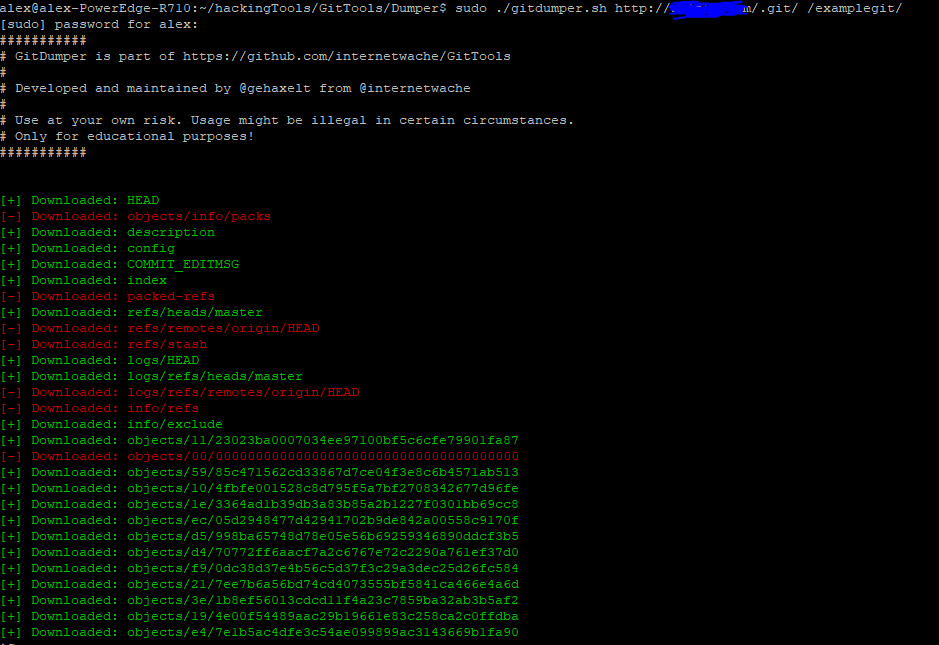
Next you manually review the source code and look for bugs, vulnerbilities, and exposed passwords. Basically treat it as a source code review.
Subversion
Subversion like Git is a revision control system and it contains a hidden folder “.svn” . This folder can also be used to recreate the source code used on the site. Simply navigate to “https://example.com/.svn”, if you see the following then the endpoint is vulnerable:
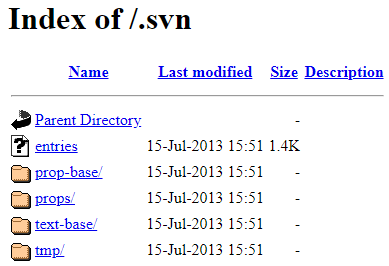
The following tool can be used to extract the files from the folder:anantshri/svn-extractor
simple script to extract all web resources by means of .SVN folder exposed over network. – anantshri/svn-extractorgithub.com
This tool will allow you to fully recreate the folder structure, source code, and other files as shown below:
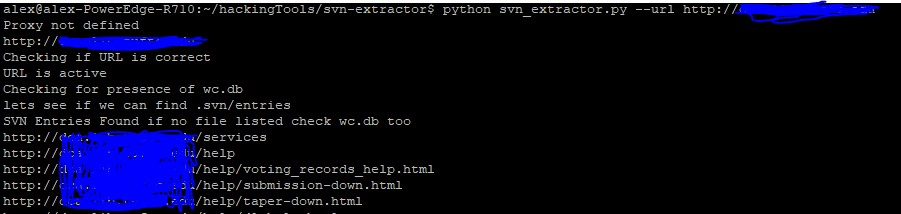
Like Git once everything is download you will manually review the source code and look for bugs, vulnerabilities, and exposed passwords. Basically treat it as a source code review.
Conclusion
The vast majority of software engineers use a revision control system. These systems contain hidden folders that hackers can use to fully recreate the source code used by the site. Once the source code is download hackers can perform a source code review looking for vulnerabilities, hard coded passwords, and much more. You should be searching for “.git” and “.svn” folders during your hunt you might find an easy win.