Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
When performing your initial recon on an organization dont forget about Github. Github is used by developers to maintain and share their code, most of the time they end up sharing much more though. Most of the organizations I come across have a public Github which can contain a tun of use full information. I have personally popped boxes using only information gained from a github account. Depending on the size of the company you can literally spend a weeks just looking for exposures on Github.
Github Dorks
You probably know what google dorks are but what are Github dorks. Github dorks are basically the same thing as google dorks. A dork is used to find specific information in a sea of information. It helps us narrow down the search to exactly what we want. We can match on file extensions , file names, or a specific set or words. This can be very handy when searching for sensitive files, API keys, passwords, and a lot more.
We can use dorks to find sensitive files that developers might have accidentally uploaded. For instance one time I was performing an external pentest against company and I was able to use github dorks to find an exposed bash_history file which had ssh passwords. This was easily done by submitting the following dork:
filename:.bash_history DOMAIN-NAME
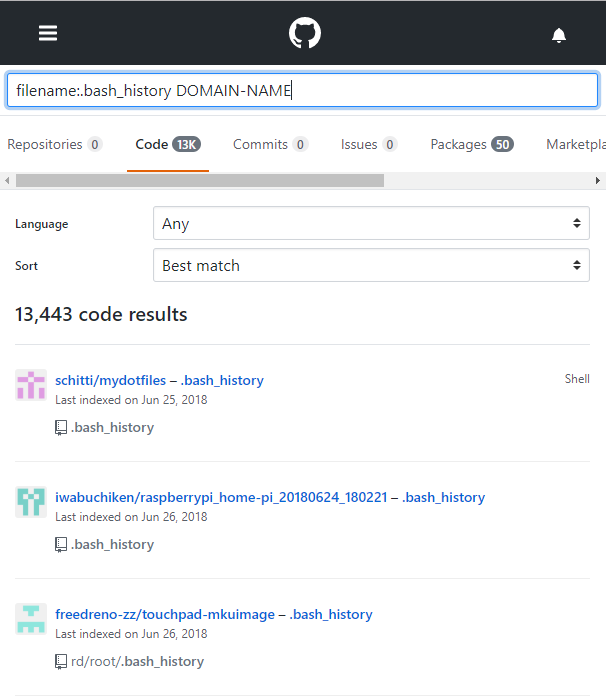
People are always uploading sensitive files to github, its a gold mine. Its also a good idea to look for exposed passwords, tokens, and api keys,usernames. Often I will search for these words followed by the company name as show below:
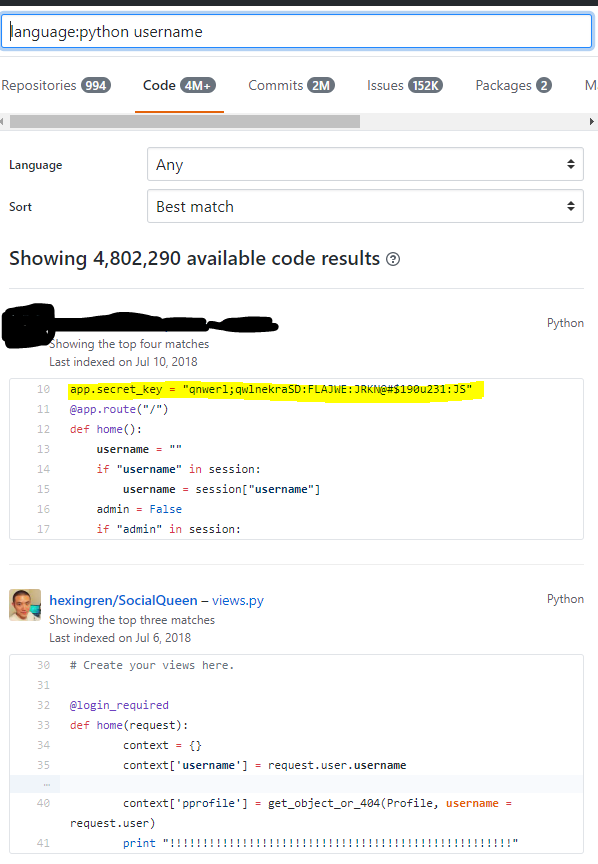
Usernames are often associated with passwords and api keys. As shown above someone is leaking their secrete key. If this was an engagement I would use that key to login to their application.
A good list of these dorks can be found below:techgaun/github-dorks
Collection of github dorks and helper tool to automate the process of checking dorks – techgaun/github-dorksgithub.com
Company Github
Instead of using Github dorks to find exposures you might want to go directly to the source. To do this you must find the companies Github page and from there you can locate all their developers and monitor their accounts.
Not all companies have a public github page but you can do a google search to find out.
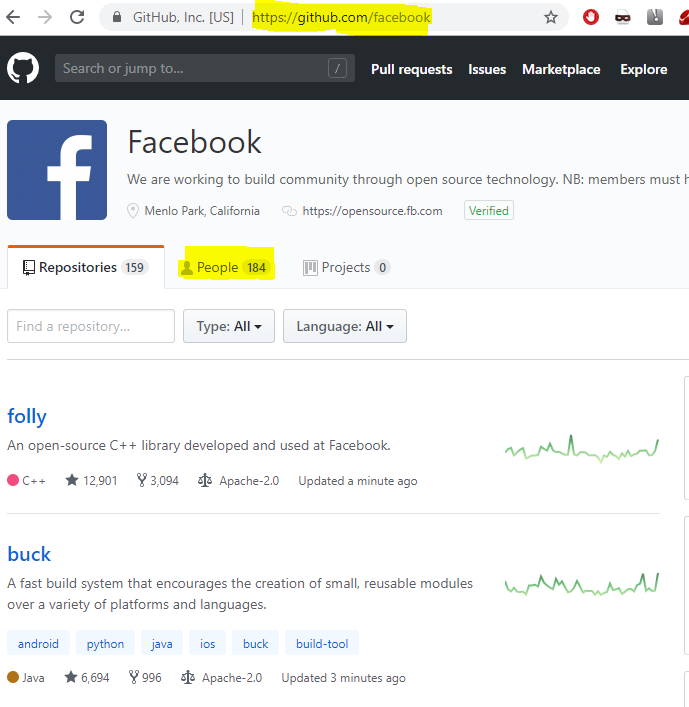
Once you find a companies page you want to get a list of people that are associated with the company. This can be done by clicking on the “people” tab.
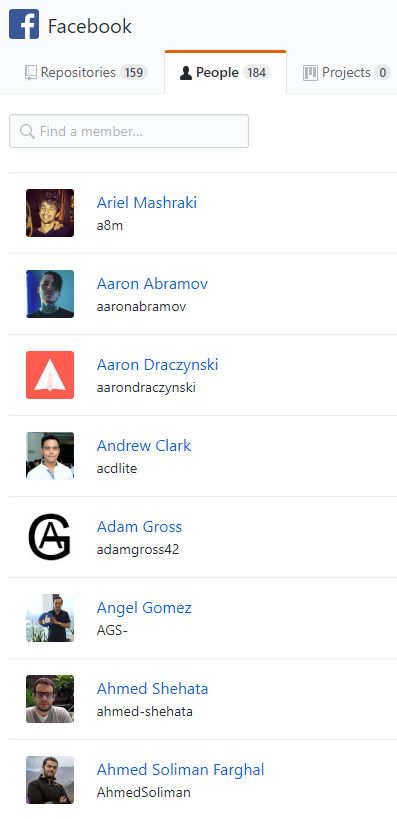
Now you will need to manually go through each one and look for exposures. Thats why this process can take so long. Facebook has 184 people and looking through each one can be boring and take along time. However, if there are a lot of people then there is a greater chance someone uploaded something they shouldnt have. You should be looking for urls, api keys, usernames, passwords, vulnerabilities, and anything else that could provide value.
Conclusion
Github is a great source of information. The vast majority of companies now a days have a Github page. If you find this page you can monitor all of their employees for sensitive exposures. You can also use Github dorks to do a broad search across all of github. You should be looking for passwords, tokens, api keys, usernames, hidden urls, or any thing else that provides value. Github is a gold mine and you should be taking advantage of it during your recon phase. OSINT for the win!