Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
Almost every website today uses javascript in some way. Jquery, anglular, react, and vue are some examples of popular javascript libraries and frameworks. Each of these contain vulnerabilities and if a website is using an outdated version they run the risk of implementing a vulnerable function that could put their entire website at risk.
Retire JS
Retire JS is an awesome tool that scans websites for outdated software. The easiest way to use this tool is to download the chrome addon. Once the addon is downloaded it will scan every site you visit in the background for outdated javascript files many of which contain known CVEs.
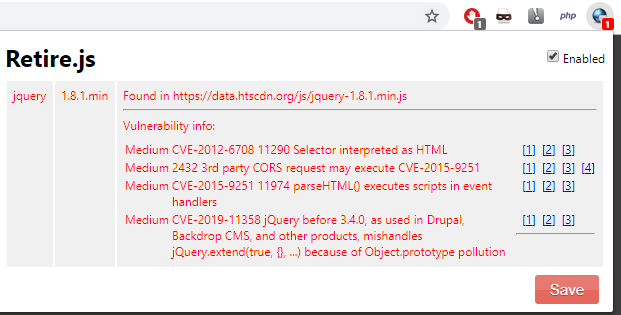
It looks like this website is using a outdated version of jqeury which has the following CVEs:
- CVE 2012–6708
- CVE 2015–9251
- CVE 2019–11358
It is important to know that just because a website imports a vulnerable javascript file doesnt mean you can exploit the vulnerability. In order to exploit the vulnerability the website must be using the vulnerable function. It is possible to import a vulnerable library without using the vulnerable function. However, even if you cant exploit the vulnerability having outdated software is always bad practice. If the site is implementing the vulnerable function then you just got yourself a win!
Custom Tools
As much as I like going to each site manually I want to automate this process a little. It would be nice if I could give it a list of bug bounty targets and have it scan all those. Retire JS was nice enough to include their datasheet on their github:RetireJS/retire.js
scanner detecting the use of JavaScript libraries with known vulnerabilities – RetireJS/retire.jsgithub.com
We can use this information to create our your own custom scanner which is exactly what I did.
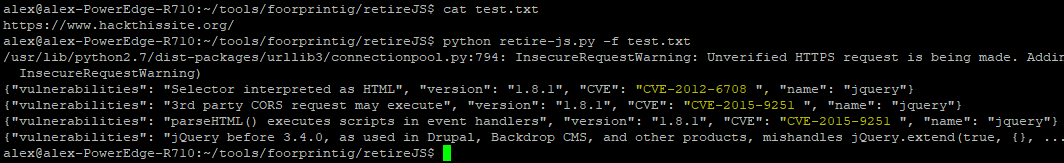
Note the script also outputs the domain and vulnerable url, I had to cut it out of the picture because it wouldn’t fit. But as you can see you get the same output as the chrome plugin but now you can mass scan hundreds of websites. My script can be downloaded below:ghostlulzhacks/RetireJs
Contribute to ghostlulzhacks/RetireJs development by creating an account on GitHub.github.com
Conclusion
99% of the internet uses javascript in their website. A lot of these sites are also using a vulnerable version of javascript which can contain known CVEs. If the website is implementing a vulnerable function then you might be able to exploit them for an easy win. Using the retirejs chrome plugin you can easily tell if a site is vulnerable. But if your doing this for bug bounties you will want to mass scan hundreds of host and thats where my script comes in. Always keep your eyes open for those pesky javascript files.