Introduction
AWS Elastic Beanstalk(EB) is an easy-to-use service for deploying and scaling web applications and services developed with Java, . NET, PHP, Node. js, Python, Ruby, Go, and Docker on familiar servers such as Apache, Nginx, Passenger, and IIS. This means we can use EB to easily deploy applications with the click of a button or shell command. AWS automates the entire deployment process.
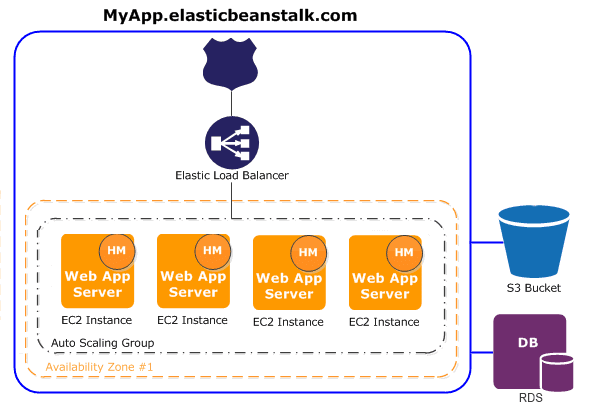
As shown in the image above you can see EB is made up of several other services such as a load balancer , an EC2 Instance AKA virtual machine, an S3 bucket, and more. EB automates the deployment of your application so developers don’t have to focus as much on the DevOps process. As a hacker this service can become a very juicy target.
Endpoints
Typically you will see the front end or API deployed to a beanstalk environment. These environments can be located by issuing the following CLI command:
- aws elasticbeanstalk describe-environments
In the image above you will see the following variable “EndpointURL”. This holds the url of the deployed EB application . Once you have this endpoint you can launch further attacks against that application such as looking for OWASP top 10 vulnerabilities if it is a web application.
Source Code
Source code is the crown jewels of intellectual property, its something most companies want to protect. When a developer deploys an application it takes the source code and saves it to an S3 bucket. Once saved it is deployed to an EC2 instance(virtual machine). This means you can find the source code of all EB applications in an S3 bucket. Anyone who has access to that S3 bucket will also have access to the source code of all EB applications.
As you can see in the image above there is an S3 bucket with the name “elasticbeanstalk”. This is where the source code is stored.
If you issue the ls command on that s3 bucket you will see a bunch of .zip files. These zip files contain the source code for the applications deployed to beanstalk. The next step is to download these files and analyze the source code for hardcoded credentials and vulnerabilities.
Environment Variables
When developers are not hard coding credentials in source code they put them in environment variables. The more secure way is to used the AWS secrete manager but you will see a lot of developers doing it this way because its a little easier to set up.
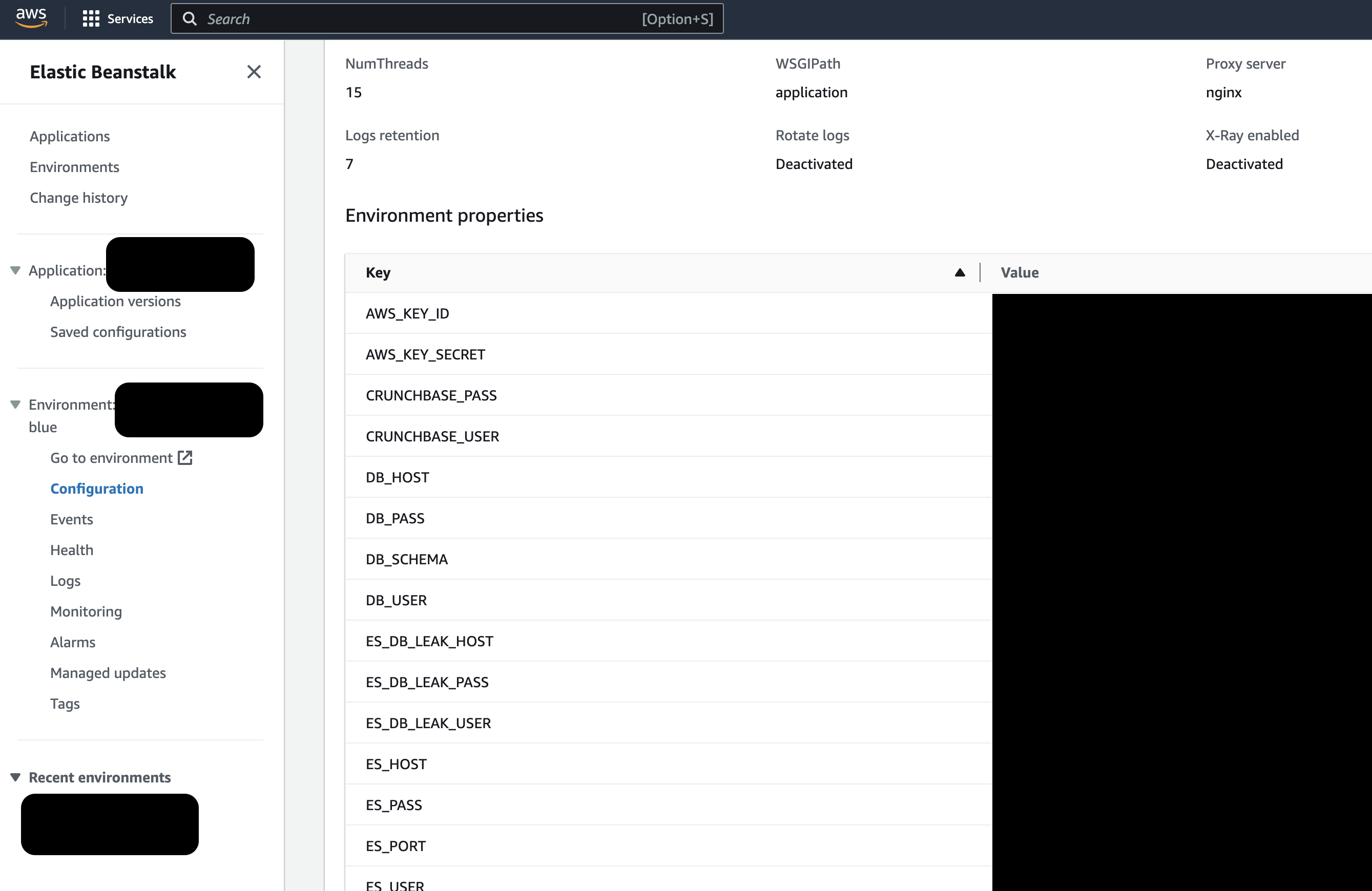
You can also grab this information via the command line tool.
- aws elasticbeanstalk describe-configuration-settings –application-name your-application-name –environment-name your-environment-name
As you can see in the image above there are lots of interesting things beings stored as environment variables. These credentials can be leveraged to compromise other systems.
Conclusion
Elastic beanstalk is a very popular service offered by AWS that allows you to deploy applications easier. As an attacker you should know that this service can hold a lot of useful information. If you ever get SSRF or access to your targets cloud environment you should review EB for source code stored in S3 buckets and interesting environment variables. We only covered a couple of things related to EB but there are many more. Ill have to cover them in a future blog post.