Slack Group
Before we get started I have started a slack group dedicated to hacking. We welcome everyone from beginner to advanced to join. I will be on everyday answer questions, doing CTFs, and talking about cool hacks. If you enjoy hacking and are looking for like minded people join below:
NEW Hacking Group Slack Channel
Introduction
Linkedin is a popular social media platform that professionals use to find jobs. Its basically an online resume that contains information such as your current job, past jobs, colleges attended , and more. This information can be very handy when targeting specific employees of a company.
Email to profile
If you happen to get ahold of your targets email you can use the Linkedin sales API to find their profile page. You do however have to be logged in to use this functionality. Sending the following requests will try to find a targets profile based on the supplied email:
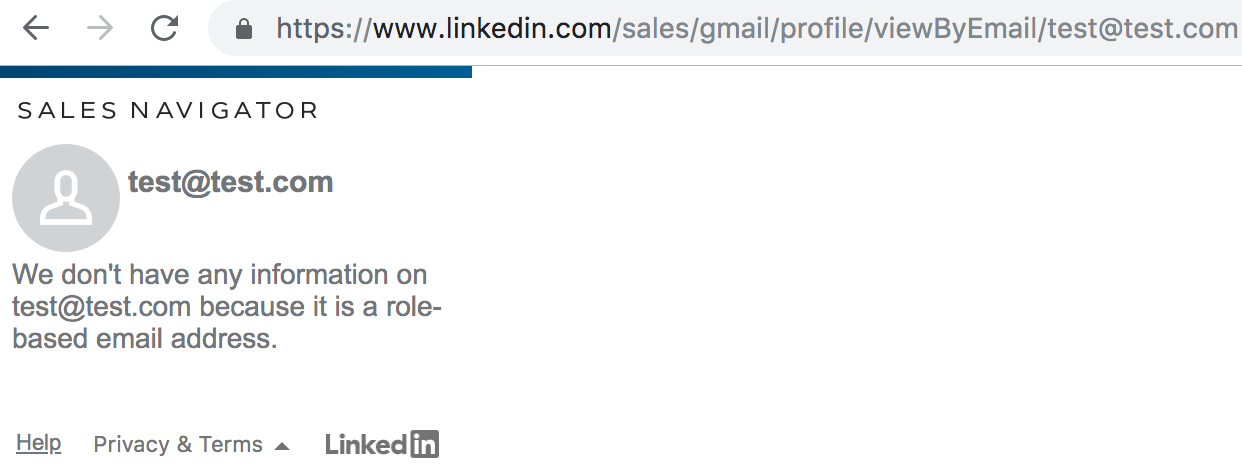
If the supplied email has an account then you will get the targets linkedin profile. This can be helpful when trying to tie an email to a person.
Company Employees
A lot of professionals and companies in America and other countries use Linkedin. It is possible to gather a list of employees, job titles, emails, and locations just by viewing a companies employee page. This information can then be when sending phishing emails.
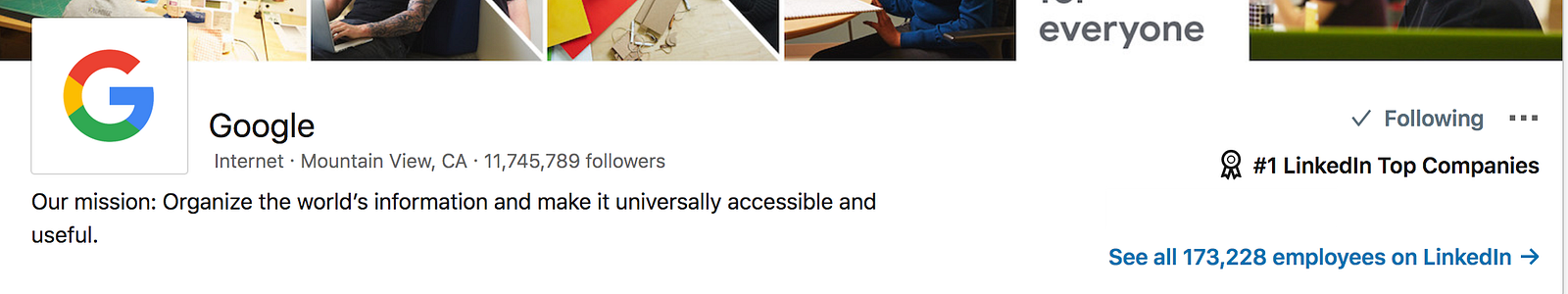
Once you find a company you just have to hit the “See all XXX employees on Linkedin” button.
You should be aware that in order to see other people profiles you generally have to have at least on mutual friend, so if your friend list is small your results will be small. Another catch is that you can only view 100 pages of results, so it will be impossible to view all 173,228 employees with one account. If you want to by pass these limitations you will need lots of accounts that have big friend lists.
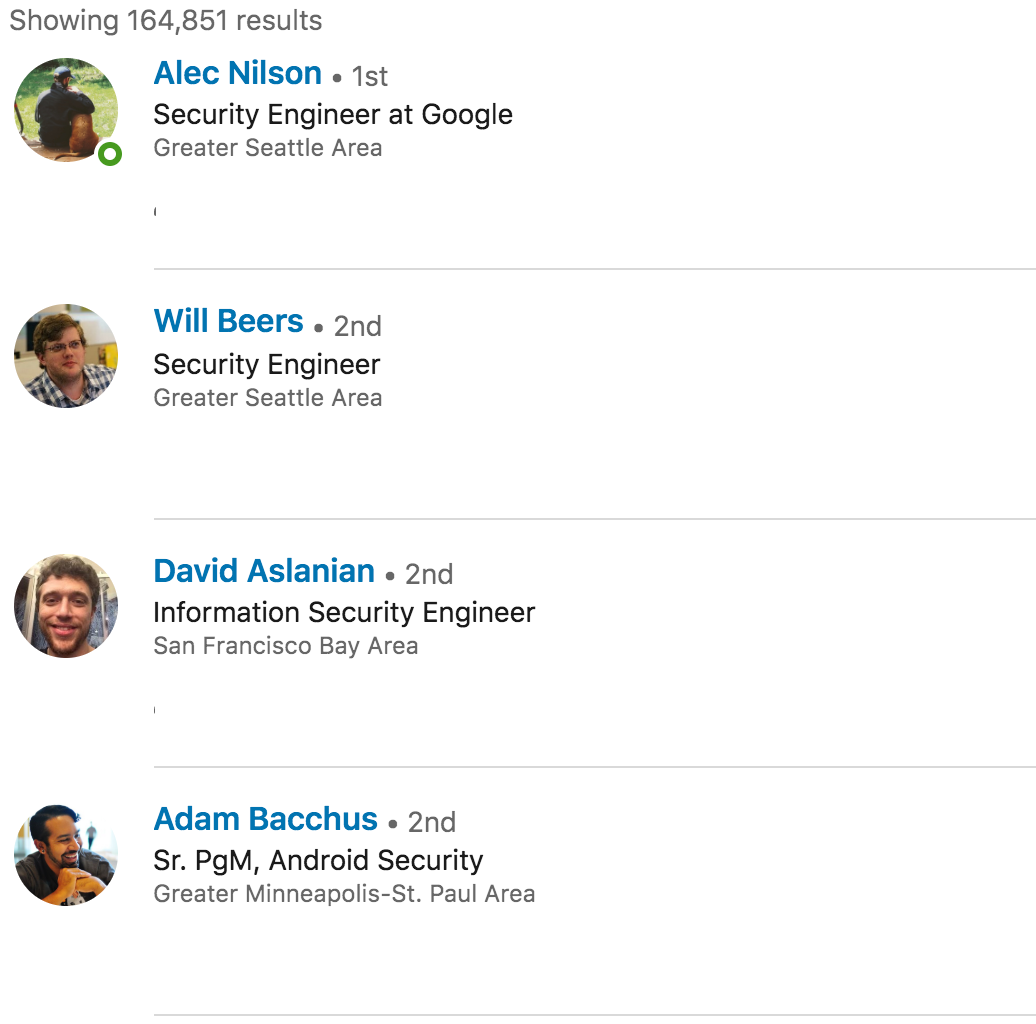
As you can see we get the employees first name, last name, job title, and location. All this is great stuff but we need their email as well so we can launch phishing campaigns.
Most companies use a standard email format such as [email protected] . You can try to find out their email format your self or you can use the following query to provide you with their email format.
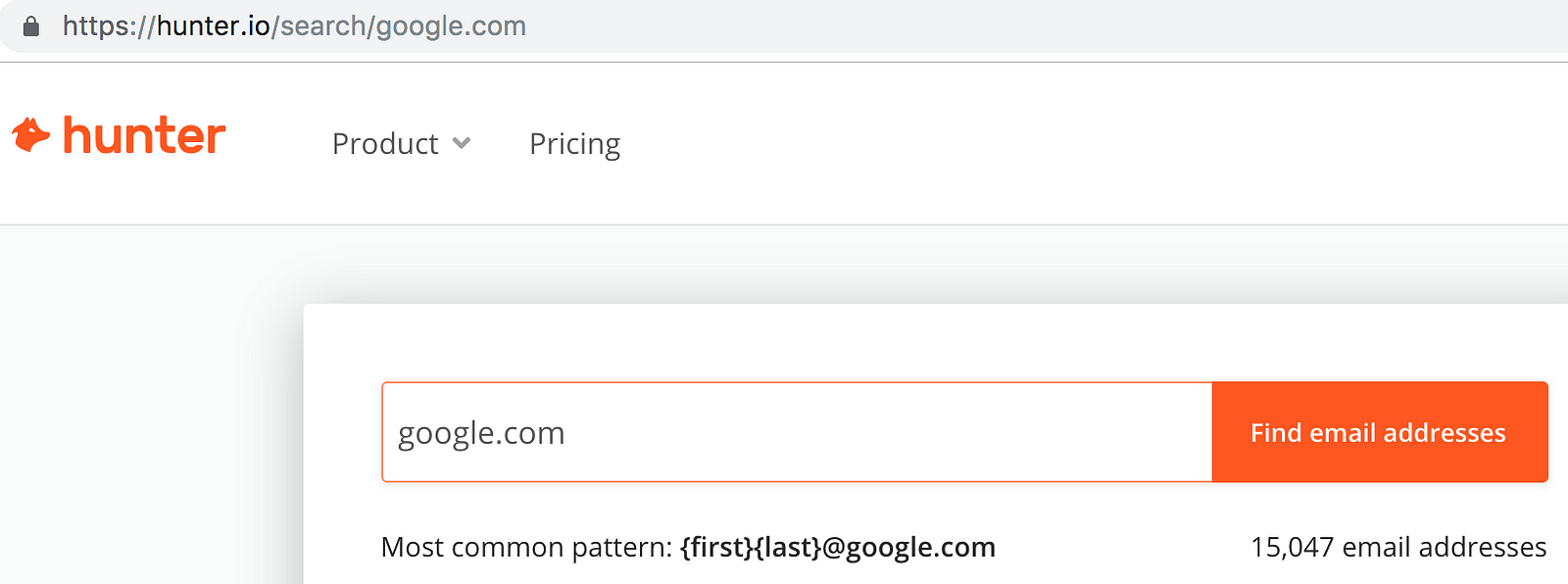
Looks like they have the email format of <firstName><lastName><@comapny.com>. All you have to do is use take the first and last name from the users linkedin profile and you should be able to create their associated work email.
I should probably say that Linkedin prohibits scrapping of their site. That being said the only way to generate a good list is to create a web scrapper and automate the whole process. After that you should have a good list of phishing targets.
Conclusion
Linkedin is a great resource of OSINT. If only have an email address you can use Linkedin to tie it back to a real person. Linkedin is also good when performing recon on an entire organization. You can find all employees that work for the target company and you can gather their names, job titles, locations, and emails. If your trying to generate a good phishing list there is no better resource.